Raspberry Pi Console Server Phase 2 – Remote Access
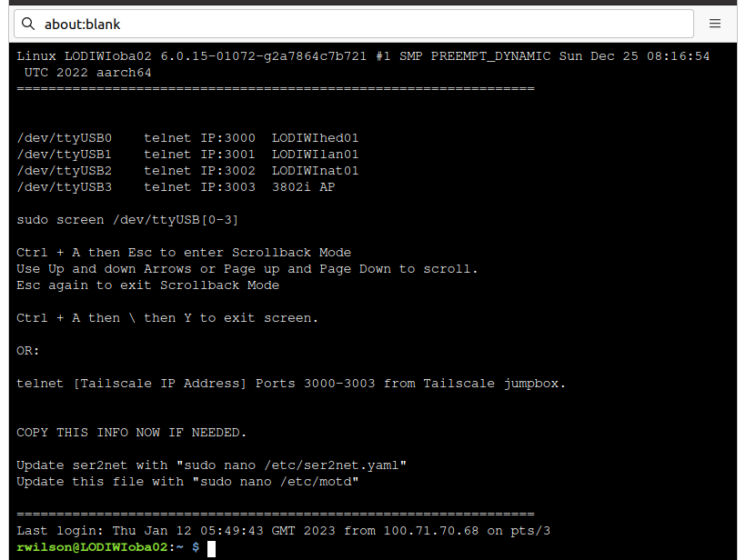
The Pi Console Server setup can be found here.
I had a working proof of concept Console Server, but no Out-Of-Band Remote Access to it yet. I wanted the solution to be Out-Of-Band ideally managed by a third party. My initial ideas were to buy a managed solution either directly from a cellular provider, or as a SD-Wan solution. After a few chats, I wasn’t finding a cheap turn key solution like I had hoped for. A colleague who I had shown my Console Server to suggested I look into Tailscale. I had never heard of it.
The explanation below was shamelessly stolen from their documentation:
What is Tailscale
Tailscale is a modern VPN built on top of Wireguard. It works like an overlay network between the computers of your networks – using NAT traversal.
Everything in Tailscale is Open Source, except the GUI clients for proprietary OS (Windows and macOS/iOS), and the control server.
The control server works as an exchange point of Wireguard public keys for the nodes in the Tailscale network. It assigns the IP addresses of the clients, creates the boundaries between each user, enables sharing machines between users, and exposes the advertised routes of your nodes.
A Tailscale network (tailnet) is private network which Tailscale assigns to a user in terms of private users or an organisation.
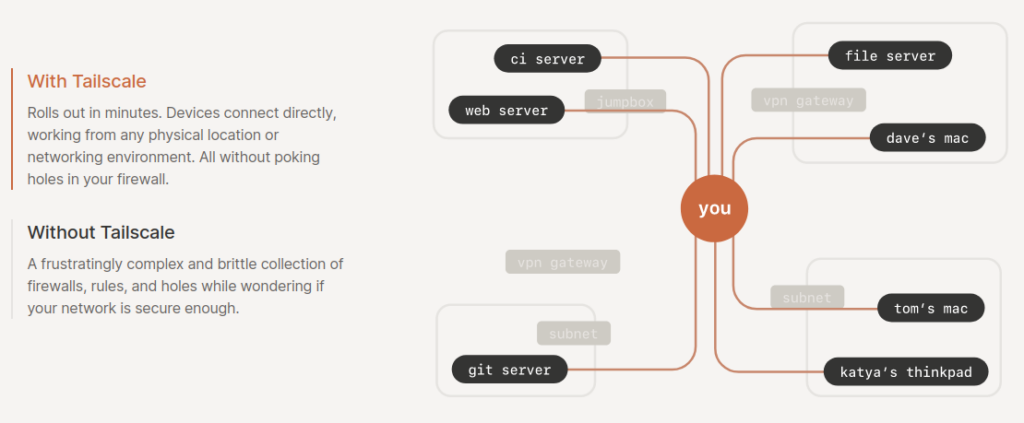
This was the perfect solution. Very simple setup with no additional hardware required. The clients will establish their connection through any internet connection creating an encrypted VPN overlay. We could use it in-band using whatever the site has for internet access (but bypassing our enterprise equipment) or out-of-band with a dedicated DSL or cellular connection.
For my test, I installed Tailscale on a Raspberry Pi I am running Pi-Hole on. This functions as my jump box. Then I installed it on two Raspberry Pi boxes I am running as test console servers. While these boxes are physically located next to each other they are on different networks requiring traffic to traverse NAT and flow through Chicago to reach each other.
The screenshot below shows looking at the status of my devices and then opening a reverse telnet session on a remote device from the jump device:
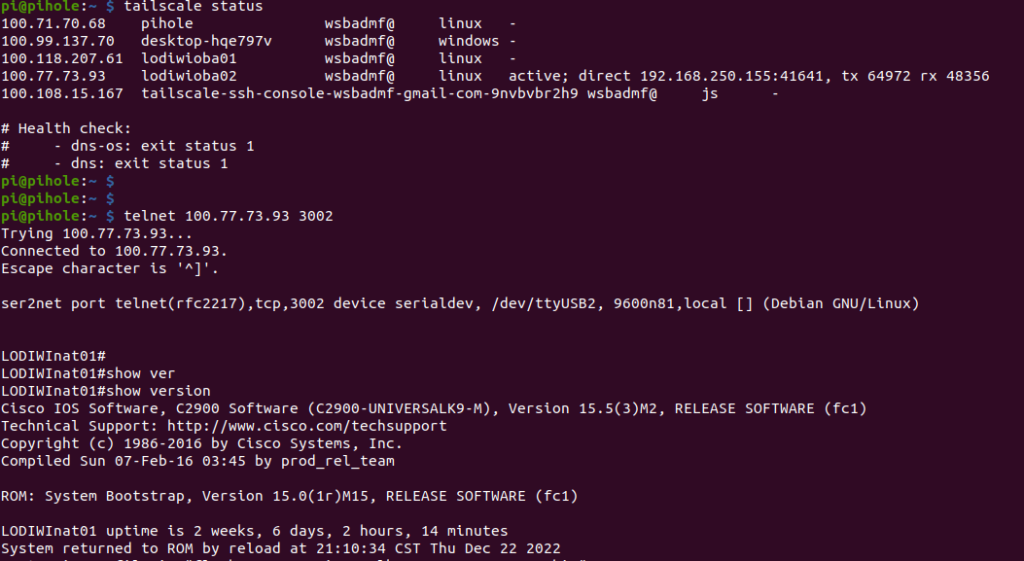
I can share this screenshot because those IPs are only reachable within my Tailnet. Even if they were not, those IPs are non-routable because they are reserved for Carrier-Grade NAT use. A whois of those IPs tells you Netname: SHARED-ADDRESS-SPACE-RFC6598-IANA-RESERVED.
Additionally, reverse telnet between hosts in the tailnet is safe because all traffic is encrypted by Wireguard, and the SSH traffic to the jump box is encrypted by SSH.
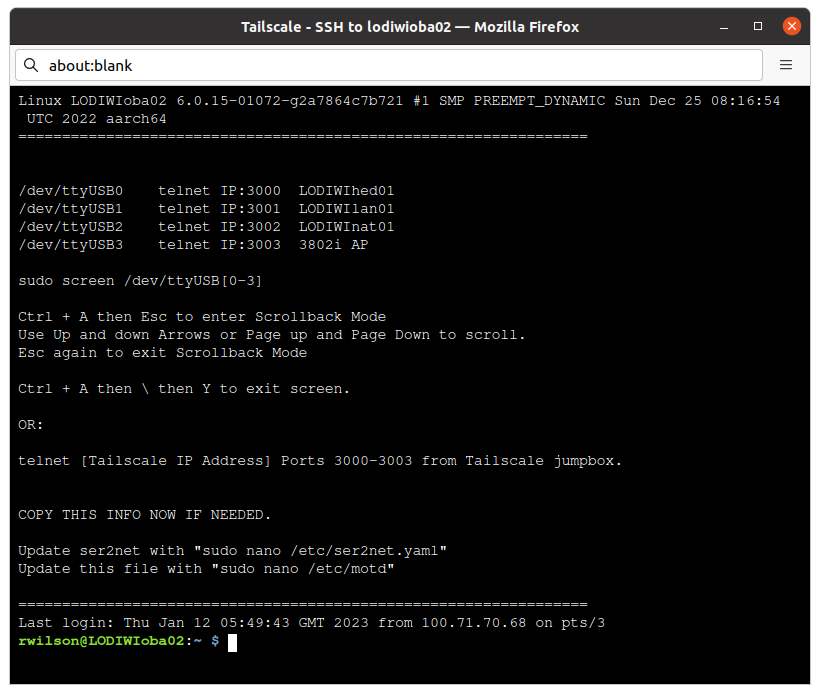
If I am not able to reach my jump box, I can install Tailscale on my Windows workstation, a Mac, a cellphone, or I have the option of opening a SSH session directly in my browser from my Tailscale admin page, thus giving secure out of band access to all console servers from anywhere.
A screenshot of a SSH session from the browser:
So far in my testing everything works perfect.